Kerberos Authentication
Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. Kerberos Authentication Steps.

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base
1 day ago the latest.

Kerberos authentication
. And Pulsar uses the Java Authentication and Authorization Service JAAS for SASL configuration. You need to provide JAAS configurations. Kerberos ˈ k ɜːr b ər ɒ s is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. The user database in this case is on the Domain Controller DC.Kerberos is a network authentication protocol. In Pulsar you can use Kerberos with SASL as a choice for authentication. In Remedy Single Sign On it is possible to configure a Kerberos as the authentication service. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials.
Oct 12 2016 kerberos authentication supports a delegation mechanism that enables a service to. Kerberos provides strong authentication for clientserver applications by using secret-key cryptography. Kerberos Authentication The target computer or domain controller challenge and check the password and store password hashes for continued use. Accessing a Kerberos-protected or Kerberized system requires an electronic Kerberos ticket which may be obtained using an HPCMP Kerberos Client Kit or through the HPC Portal.
Kerberos integration is also supported by Remedy Single Sign On which is the main authentication module that is used for a great number of BMC products. In Kerberos Authentication server and database is used for client authentication. As she flailed outside the top 25 it was fair to wonder what the future held for her at 33 years old. It has also become a standard for websites and Single-Sign-On implementations across platforms.
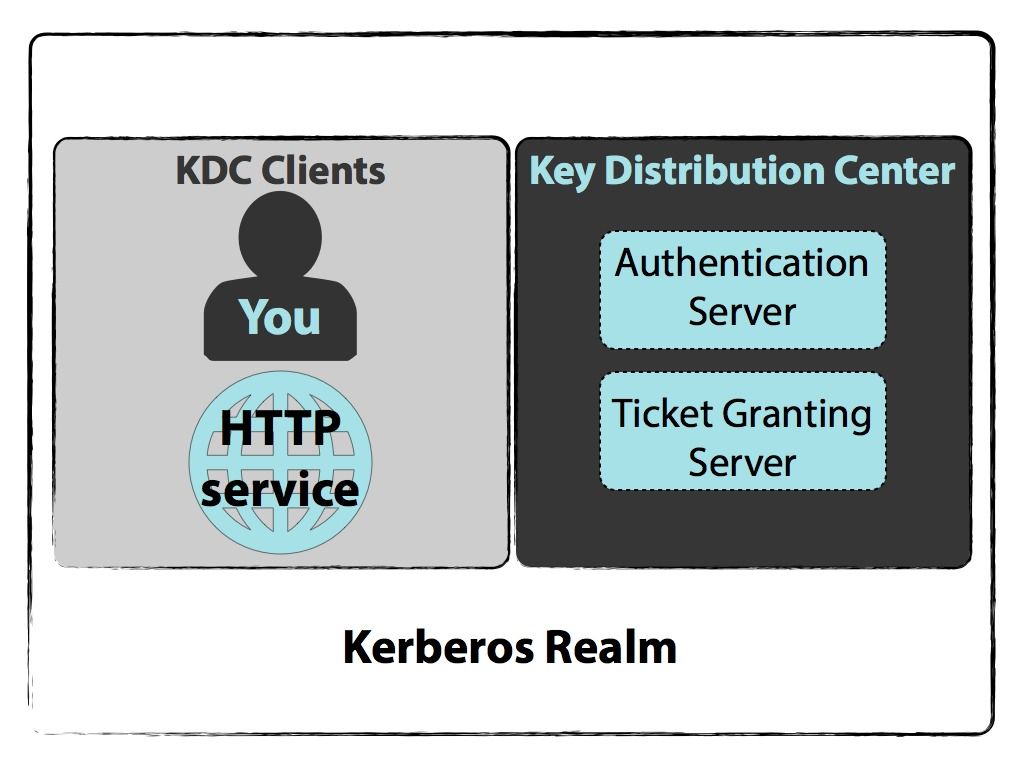
By using secret-key cryptography Kerberos is designed to provide strong authentication for client applications and server applications. Kerber keeps run at 2nd us open title alive. Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. Kerberos is a network authentication protocol.
Wie Funktioniert Die Kerberos Authentifizierung - This secret key is known only to the kdc and the service principal on each ibm streams resource. Kerberos is the default protocol used when logging into a Windows machine that is part of a domain. The oracle kerberos authentication adapter utilities are designed for an oracle client with oracle kerberos authentication support installed. The User Sends a Request to the AS.
Kerberos is an authentication protocol. Setting up Windows Authentication based on the Kerberos authentication protocol can be a complex endeavor especially when dealing with scenarios such as delegation of identity from a front-end site to a back-end service in the context of IIS and ASPNET. It is designed for client-server applications and requires mutual verification. Kerberos Authentication is a multi-step process.
Kerberos authentication for JDBC data sources. A SPNEGOKerberos or basic authentication challenge can generate a HTTP 401. The protocol was named after the character Kerberos or Cerberus from Greek mythology the ferocious three-headed guard dog of Hades. You can configure your Open Liberty server to use Kerberos credentials to authenticate to a database that is backed.
Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. The protocol was initially developed by MIT in the 1980s and was named after the mythical. This alternative method uses a browser login box that is triggered by an HTTP 401 response to collect credentials. Microsoft introduced their version of Kerberos in Windows2000.
A free implementation of this protocol is available from the Massachusetts Institute of Technology. Follow this articles steps to set up the delegation of authentication tickets and use. Let us say a user wishes to access a network file server to read a document. Negotiate is a provider or container which supports Kerberos protocol and it also contains NTLM as a.
Access Policy Manager APM provides an alternative to a form-based login authentication method. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services. Its designed to provide secure authentication over an insecure network. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography.
Each user and service on the network is a. Kerberos at its simplest is an authentication protocol for clientserver applications. The user issues an encrypted request to the Authentication Server. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication.
Kerberos is a network authentication protocol through which a client and server can authenticate one another by communicating with a trusted third-party Key Distribution Center KDC. 1 and winner of three grand slam tournaments she made her profe. Below are the steps required to authenticate through Kerberos. About basic authentication and Kerberos end-user logon.
Garden tractor pulling parts kohler command parts tractor pulling cnc machining lathe billet aluminum cam grind grinding.

Kerberos Architecture Computer Help Windows Server Microsoft

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Configuring Kerberos Authentication In Different Browsers Browser Internet Options Web Server

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux
Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

Mongodb Authentication With Kerberos Regular Expression Data Storage Reading

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony
Kerberos is a network authentication protocol. Setting up Windows Authentication based on the Kerberos authentication protocol can be a complex endeavor especially when dealing with scenarios such as delegation of identity from a front-end site to a back-end service in the context of IIS and ASPNET.

Mongodb Authentication With Kerberos Regular Expression Data Storage Reading
By using secret-key cryptography Kerberos is designed to provide strong authentication for client applications and server applications.

Kerberos authentication
. In Kerberos Authentication server and database is used for client authentication. Oct 12 2016 kerberos authentication supports a delegation mechanism that enables a service to. Accessing a Kerberos-protected or Kerberized system requires an electronic Kerberos ticket which may be obtained using an HPCMP Kerberos Client Kit or through the HPC Portal. The user issues an encrypted request to the Authentication Server.The protocol was named after the character Kerberos or Cerberus from Greek mythology the ferocious three-headed guard dog of Hades. Kerberos provides strong authentication for clientserver applications by using secret-key cryptography. The oracle kerberos authentication adapter utilities are designed for an oracle client with oracle kerberos authentication support installed. Kerberos is the default protocol used when logging into a Windows machine that is part of a domain.
Kerberos authentication is currently the default authorization technology used by Microsoft Windows and implementations of Kerberos exist in Apple OS FreeBSD UNIX and Linux. Garden tractor pulling parts kohler command parts tractor pulling cnc machining lathe billet aluminum cam grind grinding. Let us say a user wishes to access a network file server to read a document. About basic authentication and Kerberos end-user logon.
Kerberos is a network authentication protocol. In Pulsar you can use Kerberos with SASL as a choice for authentication. 1 and winner of three grand slam tournaments she made her profe. You can configure your Open Liberty server to use Kerberos credentials to authenticate to a database that is backed.
You need to provide JAAS configurations. Kerberos at its simplest is an authentication protocol for clientserver applications. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Its designed to provide secure authentication over an insecure network.
Access Policy Manager APM provides an alternative to a form-based login authentication method. Microsoft introduced their version of Kerberos in Windows2000. It has also become a standard for websites and Single-Sign-On implementations across platforms. The User Sends a Request to the AS.
A SPNEGOKerberos or basic authentication challenge can generate a HTTP 401. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials. Below are the steps required to authenticate through Kerberos. The protocol was initially developed by MIT in the 1980s and was named after the mythical.
Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. Kerberos integration is also supported by Remedy Single Sign On which is the main authentication module that is used for a great number of BMC products. In order to setup Kerberos for the site make sure Negotiate is at the top of the list in providers section that you can see when you select windows authentication. Each user and service on the network is a.
In Remedy Single Sign On it is possible to configure a Kerberos as the authentication service. Kerberos Authentication is a multi-step process. As she flailed outside the top 25 it was fair to wonder what the future held for her at 33 years old. Kerberos Authentication The target computer or domain controller challenge and check the password and store password hashes for continued use.
The user database in this case is on the Domain Controller DC. And Pulsar uses the Java Authentication and Authorization Service JAAS for SASL configuration. This alternative method uses a browser login box that is triggered by an HTTP 401 response to collect credentials. Kerberos is an authentication protocol.
Follow this articles steps to set up the delegation of authentication tickets and use. Kerber keeps run at 2nd us open title alive. Kerberos authentication for JDBC data sources. Kerberos is a network authentication protocol through which a client and server can authenticate one another by communicating with a trusted third-party Key Distribution Center KDC.
Negotiate is a provider or container which supports Kerberos protocol and it also contains NTLM as a. It is designed for client-server applications and requires mutual verification. A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services.
Wie Funktioniert Die Kerberos Authentifizierung - This secret key is known only to the kdc and the service principal on each ibm streams resource. Kerberos ˈ k ɜːr b ər ɒ s is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner.

Part2 Step By Step Guide For Configuring Kerberos Authentication In Sharepoint 2013 2016 Sharepoint Microsoft Dynamics Step Guide

Flink Configuring Kerberos Authentication Huawei Enterprise Support Community Unified Communications Public Security Ip Telephony

Kerbrute A Tool To Perform Kerberos Pre Auth Bruteforcing Cyber Security 20 Years Old Linux

Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Request Sharepoint Base

Kerberos Architecture Computer Help Windows Server Microsoft

Explain Like I M 5 Kerberos Lynn Root Explained Words Cryptography

How Do I Use Ntlm Or Kerberos Authentication To Access A Cifs Share In 2021 Trust In Relationships Messages Access

Configuring Kerberos Authentication In Different Browsers Browser Internet Options Web Server
Posting Komentar untuk "Kerberos Authentication"